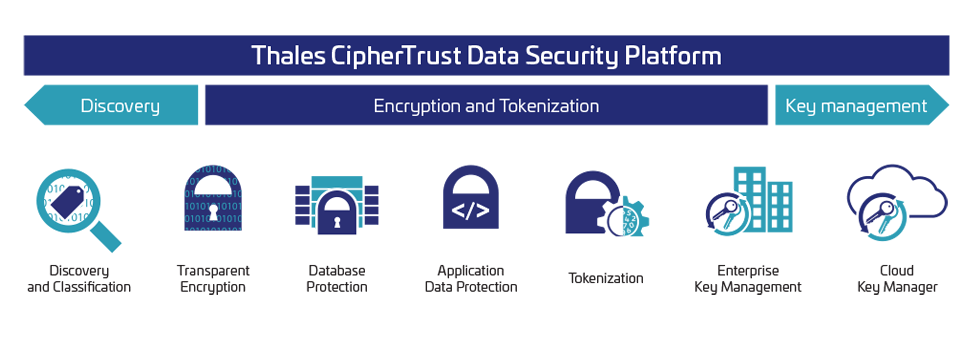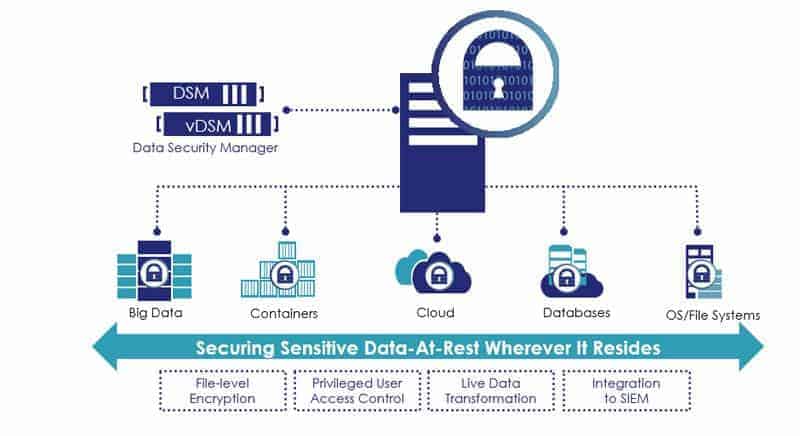
Rethinking data security: 5 ways encryption can help to protect your data - ZNetLive Blog - A Guide to Domains, Web Hosting & Cloud Computing

Data Security Encryption Ppt Powerpoint Presentation Gallery Format Ideas Cpb | Presentation Graphics | Presentation PowerPoint Example | Slide Templates